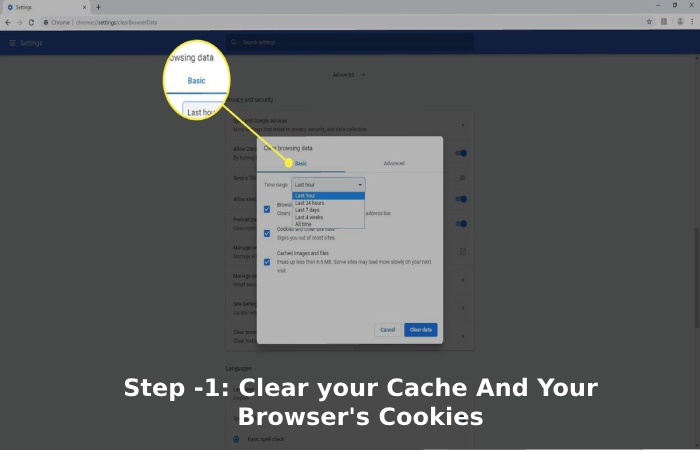
Craigslist (stylized as craigslist) is an American-categorized commercials website with sections committed to jobs, housing, on the market, objects wanted, services, community providers, gigs, résumés, and dialogue boards.
Craig Newmark began the provision in 1995 as an email distribution list to friends, offering neighborhood events in the San Francisco Bay Area. It became an internet-based provider in 1996 and expanded into different classified classes. It increased to other U.S. And Canadian towns in 2000 and now covers 70 international locations.
Antiquity craigslist
Having found people helping one another in friendly, social, and trusting communal ways on the Internet via the WELL, MindVox, and Usenet, and feeling remoted as a relative newcomer to San Francisco, Craigslist founder Craig Newmark was determined to create something comparable for nearby activities.
So, in early 1995, he started an email distribution list to pals. Most of the early postings have been submitted by Newmark and were notices of social occasions of hobby to software programs and Internet builders living and running inside the San Francisco Bay Area.
The range of subscribers and postings proliferated thru phrase of mouth. There became no moderation, and Newmark turned into surprise while human beings started using the mailing listing for non-event postings. People seeking technical positions determined that the listing turned into an excellent manner to attain humans with the competencies they had been seeking.
This brought about the addition of a jobs class. User call for more excellent categories brought on the listing of courses to grow. The initial era encountered a few limits, so in June 1995, Majordomo was set up, and the mailing list “Craigslist” resumed operations. Community participants commenced soliciting a web interface. Newmark registered “craigslist.Org,” and the internet site went live in 1996.
Craigslist
In the autumn of 1998, the name “List Foundation” was added, and Craigslist started transitioning to using this call. In April 1999, while Newmark discovered different agencies called “List Foundation,” using this call turned into dropped. Craigslist became incorporated as a private for-income employer in 1999.
Around the time of these activities, Newmark found out the web page grew so speedy that he could stop operating as a software engineer and commit his whole interest to jog Craigslist. By April 2000, nine personnel had been working out of Newmark’s San Francisco condominium.
In January 2000, contemporary CEO Jim Buckmaster joined the corporation as lead programmer and CTO. Buckmaster contributed to the web page’s multi-city structure, seek engine, dialogue boards, flagging system, self-posting technique, homepage design, personals categories, and quality-of-Craigslist characteristics. He was endorsed to CEO in Nov 2000.
Craigslists org
The internet site expanded into nine extra U.S. Cities in 2000, 4 in 2001 and 2002, and 14 in 2003. On August 1, 2004, Craigslist started charging $25 to publish job openings on the New York and Los Angeles pages. On an equal day, a brand new section referred to as “Gigs” was delivered, in which low-price and unpaid jobs could be posted for free.
In March 2008, Spanishs, French, Italians, German, and Portuguese became the primary non-English languages Craigslist supported. As of August nine, 2012, over 700 towns and areas in 70 international locations had Craigslist websites.
Craigslist sites massive cowl regions in preference to character metropolitan areas—for example, the U.S. States of Delaware and Wyoming, the Colorado Western Slope, the California Gold Country, and the Upper Peninsula of Michigan. Craigslist websites for some massive towns, including Los Angeles, additionally consist of the user’s capacity to recognize a specific location of a metropolis (together with crucial Los Angeles).
Actions craigslist
The website serves more than 20 billion page views per month, setting it in 72nd area standard among international websites and eleventh location usual among websites inside the United States (according to Alexa.Com on June 28, 2016), with extra than forty-nine. There are four million precise month-to-month visitors in the United States (per Compete.Com on January 8, 2010). With more than eighty million new categorized commercials each month, Craigslist is the leading classifieds provider.
The web page gets extra than 2 million new job listings each month, making it one of the pinnacle job boards in the international. The 23 biggest U.S. Cities indexed on the Craigslist home web page collectively get hold of greater than 300,000 postings in line with day simply in the “for sale” and “housing” sections as of October 2011. The classified ads vary from traditional purchase/sell commercials and community announcements to non-public advertisements.
Financials and possession
In DEC 2006, at the UBS Global Media Meeting in New York, Craigslist CEO Jim Buckmaster informed Wall Street analysts that Craigslist had little interest in maximizing income and, as an alternative, favored helping users discover vehicles, apartments, jobs, and dates.
Craigslist’s main sales supply is paid process commercials in pick-out American towns. The organization no longer officially discloses financial or ownership records. Nevertheless, analysts and commentators have pronounced various figures for its annual revenue, ranging from $10 million in 2004, $20 million in 2005, and $25 million in 2006 to probable $ hundred and fifty million in 2007.
Fortune has defined its revenue version as “quasi-socialist,” citing its awareness of capabilities for customers irrespective of profitability. On the other hand, Eric Baker of StubHub has defined the web page as an “ability gold mine of revenue if most effective it would abandon its communist manifesto.”
Financials craigslist
On August thirteen, 2004, Newmark announced on his weblog that auction giant eBay had purchased a 25% stake in the employer from a former employee. Some enthusiasts of Craigslist expressed the issue that this improvement could affect the website’s longtime non-industrial nature. As of April 2012, there had been no noticeable modifications to the website’s usefulness or the non-advertising and marketing nature; neither banner ads nor expenses for some offerings were supplied to organizations.
The organization became believed to be owned principally with the aid of Newmark, Buckmaster, and eBay (the three board members). eBay owned approximately 25%, and Newmark is assumed to very own the most significant stake
In April 2008, eBay announced it became suing Craigslist to “protect its four-year monetary funding.” eBay claimed that in January 2008, Craigslist executives took moves that “unfairly diluted eBay’s monetary interest by more than 10%”.
Financials craigslist org
Craigslist filed a counter-healthy in May 2008 to “remedy the significant and ongoing damage to honest opposition” that Craigslist claimed was constituted through eBay’s actions as Craigslist shareholders; the business enterprise contended that it had used its minority stake to gain get entry to confidential statistics, which it then used as part of its competing provider Kijiji.
On June 19, 2015, eBay Inc. Announced that it might divest its stake lower back to Craigslist for an unknown quantity and settle its litigation with the enterprise. Unfortunately, the move got here shortly before eBay’s planned spin-off of PayPal and an attempt to divest other gadgets to the cognizance of its core business.
Content policies craigslist
The Swedish luxurious market internet site Jameslist.Com acquired a lawsuit filed on July 11, 2012, which, among unspecified damages, additionally asked for a complete shutdown of Jameslist.Com As an outcome, the younger enterprise changed into pressured to rename to JamesEdition.
As of 2012, mashup websites such as padmapper.Com and housingmaps.Com overlapped Craigslist information with Google Maps and included search filters to enhance usability. In June 2012, Craigslist modified its terms of service to disallow the practice. In July 2012, Craigslist filed a lawsuit against padmapper.Com. Following the shutdown of Padmapper.Com, a few users complained that the service was helpful and should have remained intact.
Why Craigslis Is Such a Mess
With more than forty-seven million precise users every month inside the U.S. by myself – nearly a fifth of the kingdom’s grownup population – it is the most vital network site going and yet the most underdeveloped.
Photo: PLATON * The Internet’s fantastic promise is to make the arena’s facts universally reachable and beneficial. So how come while you arrive on the maximum famous relationship web page within the U.S., you find circulation of nameless come-ons intermixed with insults, advertisements for prostitutes, naked photos, and apparent scams? In a layout straight from the Web’s earliest days, miscellaneous posts compete for attention on page after page of blue links, undifferentiated by using tags, rankings, or even usernames. Millions of humans seemingly trust that love awaits right here, but it’s miles adequately hidden. Is this honestly the quality we can do?
Odd, perhaps, but no stranger than what you see at the most popular process-search website online: another wilderness of hypertext links, one line after another, without recommendations, networking functions, or maybe safety towards replica postings.
Subject to an incredibly unpredictable filtering machine that produces each day outrage amongst humans whose help-wanted advertisements had been removed without clarification, this website no longer most effective beats its competitors—Monster, CareerBuilder, Yahoo’s HotJobs—however, it garners more significant site visitors than all of them blended. So are our requirements, without a doubt, so low?
Why Craigslit
But if you need to peer a large number, move to go to the nation’s finest apartment-hunting website online, the first possible preference of everybody looking for an apartment or a roommate. On this web page, opposite to every precept of usability and not unusual experience, you can’t easily browse pix of the residences for rent. Customer aid? Visit the help desk in case you enjoy being insulted. How lots of a market proportion does this housing site have? In many cities, a large percentage. It isn’t always worth comparing its site visitors to competitors due to the fact at this scale, there is not any competition.
Each of these websites of the route is merely one of the many sections of craigslist, which dominates the marketplace in facilitating face-to-face transactions, whether or not people are connecting to shop for and promote, give something away, lease a condominium, or have some intercourse.
With extra than 47 million precise users every month within the U.S. by myself—almost a 5th of the nation’s grownup populace—it’s miles the essential community website going and yet the smallest. Think of any Web nose that has become famous in the past ten years: Chances are craigslist considered it and rejected it. If you try to construct a 3rd-celebration utility designed to make craigslist paintings higher, the management will almost certainly throw up technical roadblocks to close you down.
Craigslist Is Such a Mess
Craigslist isn’t the handiest tremendous in scale and proof against enterprise cooperation; it is also, on the whole, unfastened. The only things that cost cash to submit at the website are process commercials in some cities ($25 to $ seventy-five), apartment listings with the aid of agents in New York ($10), and—in a unique case born of new prison problem—commercials in categories usually used by prostitutes because government inspires providers to preserve a document that might resource investigators. There is no banner advertising and marketing. They won’t assist you to be a part of them, and you can’t beat them both at this charge.
In instances, it has taken place to human beings that the problems with craigslist will be solved by using attractive to its eponym, Craig Newmark. Unfortunately, Newmark has been under lots of strain in recent times. His organization is being sued via eBay, a competitor and minority shareholder indignant at being excluded from the organization’s deliberations.
The attorney preferred of South Carolina has blustered about prosecuting his CEO for facilitating prostitution, and there had been robust, demanding situations from law enforcement corporations in different states, too. The tabloids have relentlessly played up testimonies of approximately two so-known craigslist killers, people who allegedly used the website online’s erotic-services section to entice victims and some others who used the assist-wanted advertisements.
Newmark responds to such grievances with excessive serenity. Inquire approximately his budget, and he talks around about his hummingbird feeder. Then, when his Twitter web page asks him, “What are you doing?” he retweets inside the voice of a squirrel.
“Run, run, run,” he says. “Dig, dig.” craigsist
Though the business enterprise is privately held and no longer responds to questions about its price range, it’s far glaring that craigslist earns astonishing amounts of cash. One latest file, from a consulting company that counted the paid ads, estimates that revenue may want to pinnacle $one hundred million in 2009. Should craigslist ever be bought, the charge likely would run into the billions. Newmark, by this lighting, is an utterly wealthy guy.
When everybody reminds him of this, the craigslist founder says there may be nothing he would care to do with that lot of cash, ought it ever come into his fingers. He already has a parking area, a hummingbird feeder, a small domestic with a view, and a bath with solid water pressure. So what else is he supposed to want? Frustration over these sorts of replies every so often turns into comical. In a July 2007 box interview, Charlie Rose spent 1/2 of the program trying to get Newmark to admit his suitable fortune and failed. “I do not have everywhere near as a good deal manipulate as you watched,” Newmark stated.
“Dig, dig.” craigslist
“I’m no longer talking how much manipulate; I’m talking percent of possession,” Rose said. Rose is usually kind to his visitors, but the scent of unacknowledged wealth introduced his ferocity.
- “Oh, the same thing from my factor of view,” Newmark said, trying to flow the subject along.
- “Do you very own more than 50 percent of craigslist or now not?” Rose requested.
- “No.”
- “You don’t?”
- “Correct.”
- “In other phrases, other humans personal that, or you’ve got given it away or something.”
- “Could be, Charlie.”
- “OK, however, I’m—why are you so …?”
- “Coy?”
- “Yeah.”
- “It doesn’t matter,” Newmark said. “I mean …”
- “I understand it would not matter,” Rose repeated, his face a mask of pain.
Newmark’s claim of virtually general disinterest in wealth dovetails with how craigslist does commercial enterprise. Besides supplying almost all of its functions at no cost, it scorns advertising and marketing, refuses investment, ignores design, and does not innovate.
Ordinarily, a business enterprise that confirmed such disdain for the standard enterprise guidelines might be susceptible to the opposition, but craigslist has no critical rivals. The glory of the site is its length and its rate. But visible from every other perspective, craigslist is one of the strongest monopolies in records, wherein clients are locked in by way of prices set at 0 and in which the atmosphere of overlook isn’t always a manner to extract greater earnings but the expression of a worldview.
Worldview is clean to the kingdom of craigslists
The axioms of this worldview are clean to the kingdom. “People are top and trustworthy and typically simply concerned with getting through the day,” Newmark says. Suppose the general public is appropriate and their wishes are easy. In that case, altogether, you have to do to serve them well is construct a minimum infrastructure, letting them get collectively and paint matters out for themselves. Any additional features are nearly absolutely superfluous and could even be harmful.
Newmark has been operating tough to increase the impact of his worldview. His public pronouncements have the thrilled but apologetic tone of a person who has come upon secret hiding in plain sight and finds it embarrassingly necessary to point out that something that has been too lengthy was obvious. He seems to have located a new manner to run a commercial enterprise. He suspects that it can be the proper manner to run the arena.
Public-spirited and mild-mannered, politically liberal and socially awkward, Newmark has one trait that mattered greatly in craigslist’s fulfillment: He is willing to perform the equal mission over and over. During the agency’s first years, Newmark approved almost every message on the list, and in the decade, he has spent tons of his time doing away with offensive ones. Even by the full conservative accounting, he has passed judgment on tens of heaps of advertisements. Significantly few humans ought to do that and thrive.
San Francisco espresso shop craigslists
We are sitting in a San Francisco espresso shop called Reverie Café Bar, where Newmark spends long hours and has given endless interviews. Many matters in his lifestyle rely on routine. When he talks, he calls upon a range of conversational gambits he has been accumulating for all time, and he has a spread of good outcomes on his mobile smartphone, which includes a cymbal crash, that he can trigger to make it clear he’s joking. When people misunderstand him, he does not get upset. “I’m the Forrest Gump of the Cyberspace,” he says. He loves customer support. “I’ll only be doing this so long as I stay,” he says. He faucets his telephone, triggering a ghostly what, hahaha. “And after that, who is aware of it?”
An email has always been a perfect outlet for Newmark’s genial nature. Craigslist commenced in 1995 as a mailing listing with announcements of events of interest to technical human beings. As more of them started to subscribe, he advocated for readers to submit their personal information, archived the messages on a Web web page, and attempted to make sure all of the content material was legitimate.
Netscape’s IPO craigslists
After Netscape’s IPO in August of that yr, craigslist became a portal into the dot-com scene. Within two years, he had many readers, most of whom he failed to realize. Of course, this was a massive responsibility for any individual who isn’t an extrovert. “I used to electronic mail him every day,” says Christina Murphy, one of the first tech recruiters to use craigslist regularly. “If I made a mistake in an activity posting, I could have to call him and ask for an exchange. It drove him insane.”
So Murphy and an Internet consultant named Nancy Melone commenced assembly with Newmark, looking to map out an extra professional destiny for craigslist that did not require its founder to take phone calls. Job situations were an obvious source of revenue, and in 1998 they flung a nonprofit called List Foundation. Recruiters might pay $30 for advertisements, the whole lot else could be loose, and any money left after paying the fee of maintenance and administration could receive away.
Melone turned into CEO of craigslist
Melone turned into CEO. Newmark’s willingness to cede so much control involved Murphy, who soon gave up the undertaking. “It changed into a stunning, ideal little global,” she says. “And it becomes being taken over by using different forces.”
For almost 12 months, the website online came to be had at two URLs, craigslist.Org and the less embarrassingly private listfoundation.Org. But Melone and Newmark have been pulling in particular directions, or as an alternative, Melone changed into pulling, and Newmark was digging in his heels.
By the end of the last decade, the Internet frenzy changed at its height, and the neatest minds of the brand new enterprise all agreed that the proper strategy turned into to get extensive speedy in anticipation of a sale or an IPO. Melone wanted to raise costs. Newmark is worried about charging for listings at all. Melone wanted to emerge as a dotcom; Newmark became wedded to the concept that craigslist became a community provider.
Melone became gregarious craislist
Melone became gregarious, a talker. Newmark had great powers of passive resistance. A cut-up turned into inevitable, and one day in late September 1999, craigslist customers who got here through the listfoundation.Org cope with discovered themselves routinely bounced to a new, for-income Web web page called MetroVox. Run by using Melone, it offered comparable forms of community listings and had a much more aggressive plan to grow. Melone said that Newmark had authorized the switch; Newmark announced that he’d been blindsided.
This was craigslist’s first critical aggressive project, and perhaps it’s ultimate. Newmark had a few private features that must have been dead in an entrepreneur. Aside from his conversation issues and an aversion to exerting authority, he cared nothing about entrepreneurship. But within the struggle with MetroVox, he had an asset that extra than compensated for those shortcomings: For years, he had worked on his web page with an uncanny, machine-like constancy, doing all the complicated and repetitive matters that might make most people determined with frustration and indifference, and he had executed them fortuitously.
gregarious craigsli
And now his users paid him back in the most transparent way: They stopped the usage of the List Foundation cope, resumed posting their free ads at craigslist.Org, and emailed Newmark when issues occurred. Then, less than 12 months later, the bubble burst, and MetroVox dwindled.
Newmark abandoned the idea of going for walks on craigslist as a nonprofit, which might have required him to examine and comply with too many regulations. Instead, he realized that no person ought to stop him from giving his money freely if he made an excessive amount of it.
Within the interim, he surpassed many of his possessions to others to avoid acquiring an excessive amount of authority. “I become involved about going middle-elderly crazy,” he says. He additionally put top-notch distance between himself and any government duty. The modern-day CEO, Jim Buckmaster, joined the website online in 2000 as a programmer and handled each enterprise and strategic difficulty.
Buckmaster craislist
It became Buckmaster who crafted the current approach for growth—a slow, bloblike, seemingly unstoppable accretion of new craigslist towns, every an actual image of the others, released with no advertising, marketing, or publicity. Sometimes a new site grows very slowly for a long time. But in the end, listings hit a certain quantity, after which the web page becomes so familiar and critical that it is extra or less taken with no consideration utilizing every person besides the distressed publishers of nearby newspapers.
As a result, revenue from newspaper classified ads is off nearly 50 percent inside the decade, a drop that involves almost $10 billion. Only a fraction of this loss is due to Newmark’s organization, but as the most extensive online classified website, craigslist is accessible for the charge.
Because he’s the founder of an excellent Internet corporation that still happens to be supporting the country’s dailies going out of enterprise, Newmark’s opinion is eagerly sought. As a result, he spends much time at conferences and global meetings. He attempts to reply to questions about how to high-quality shield the general public from the technology of cheap and ubiquitous media. As we watch the birds on the patio of Reverie, Newmark tries out a number of the phrases he’s hoping to use within the coming months as he unfolds the lessons of craigslist. “My massive assignment is to assist make grassroots democracy as an awful lot part of our government as representative democracy,” he says.
Related Search Terms
- craigslist
- craiglist
- craigslist seattle
- craigslist phoenix
- craigslist san diego
- craigslist portland
- craigslist chicago
- craigslist houston
- craigslist denver
- craigslist los angeles
- craigslist dallas
- craigslist sacramento
- craigslist mn
- craigslist atlanta
- craigslist las vegas
- craigslist austin
- craigslist tucson
- craigslist maine
- craigs list
- craigslist pittsburgh
- craigslist tampa
- craigslist nj
- craigslist san antonio
- craigslist boston
- craigslist albuquerque
- craigslist spokane
- craigslist minneapolis
- craigslist orlando
- craigslist ny
- craigslist detroit
- craigslist sf
- craigslist nh
- craigslist boise
- craigslist philadelphia
- craigslist milwaukee
- craigslist nashville
- craigslist miami
- craigslist oahu
- craigslist new york
- craigslist cincinnati
- craigslist san francisco
- portland craigslist
- craigslist kansas city
- craigslist buffalo
- craigslist st louis
- craigslist madison
- craigslist florida
- craigslist baltimore
- craigslist rochester ny
- craigslist dc
- craigslist nyc
- craigslist vt
- craigslist reno
- craigslist ri
- craigslist colorado springs
- craigslist tulsa
- craigslist la
- craigslist cleveland
- denver craigslist
- craigslist long island
- craigslist indianapolis
- craigslist orange county
- craigslist pets
- craigslist oc
- craigslist omaha
- craigslist raleigh
- craigslist eugene
- craigslist okc
- craig’slist new york
- craigslist fresno
- seattle craigslist
- craigslist ie
- craigslist ventura
- phoenix craigslist
- craigslist modesto
- dallas craigslist
- craigslist michigan
- craigslist knoxville
- craigslist pa
- craigslist inland empire
- craigslist ct
- craigslist fort myers
- craigslist south jersey
- craigslist albany
- craigslist jacksonville fl
- san diego craigslist
- craigslist fort collins
- craigslist charlotte
- craigslist el paso
- craigslist des moines
- craigslist nc
- craigslist springfield mo
- craigslist richmond va
- craigslist sarasota
- craigslist ohio
- craigslist california
- craigslist charlotte nc
- craigslist va
- craigslist new orleans
- craigslist texas
- craigslist santa barbara
- craigslist monterey
- craigslist columbus ohio
- craigslist anchorage
- sacramento craigslist
- craigslist grand rapids
- craigslist san jose
- craigslist mcallen
- craigslist colorado
- craigslist bellingham
- craigslist asheville
- spokane craigslist
- boise craigslist
- craigslist greenville sc
- craigslist knoxville tn
- craigslist oregon
- craigslist santa fe
- craigslist yakima
- craigslist kc
- houston craigslist
- craigslist bakersfield
- craigslist raleigh nc
- craigslist missoula
- craigslist ocala
- craigslist bend
- craigslist medford
- craigslist green bay
- craigslist new jersey
- craigs
- craigslist chattanooga
- craigslist pensacola
- craigslist worcester
- craigslist syracuse
- craigslist santa cruz
- craigslist redding
- craigslist rhode island
- craigslist maui
- craigslist minnesota
- craigslist fargo
- austin craigslist
- craigslist lexington ky
- craigslist wausau
- craigslist tacoma
- craigslist akron
- craigslist greensboro nc
- craigslist columbia sc
- craigslist south florida
- chicago craigslist
- craigslist hawaii
- las vegas craigslist
- craigslist boulder
- los angeles craigslist
- craig
- craigslist jobs
- craigslist columbus
- craigslist louisville ky
- san antonio craigslist
- craigslist appleton
- craigslist corpus christi
- tucson craigslist
- craigslist western mass
- reno craigslist
- craigslist stockton
- craigslist palm springs
- craigslist wilmington nc
- craigslist fort worth
- sf craigslist
- craigslist slo
- craigslist delaware
- craigslist humboldt
- craigslist wisconsin
- craigslist buffalo ny
- oc craigslist
- craigslist bay area
- craigslist hudson valley
- craigslist cars
- pittsburgh craigslist
- craigslist bozeman
- boston craigslist
- craigslist greenville
- craigslist portland oregon
- craigslist lubbock
- cincinnati craigslist
- des moines craigslist
- buffalo craigslist
- craigslist fort wayne
- craigslist norfolk
- craigslist myrtle beach
- craigslist western slope
- craigslist wenatchee
- cragslist
- craigslist iowa
- craigslist free stuff
- maine craigslist
- craigslist washington
- craigslist jacksonville
- craigslist york pa
- craigslist louisville
- craigslist salem
- eugene craigslist
- craigslist eau claire
- atlanta craigslist
- craigslist pueblo
- craigslist kalispell
- tulsa craigslist
- craigslist duluth
- medford craigslist
- craigslist albany ny
- nh craigslist
- craigslist memphis
- craigslist usa
- craigslist lakeland
- craglist
- craigslist ma
- craigslist toledo
- craigslist tallahassee
- craigslist dayton
- craigslist austin tx
- craigslist salem oregon
- craigslist chico
- craigslist wichita
- fresno craigslist
- craigslist cape cod
- craigslist rochester mn
- craigslist san luis obispo
- milwaukee craigslist
- raleigh craigslist
- craigslist corvallis
- craigslist tri cities
- craigslist columbia mo
- craigslist las cruces
- craigslist eastern nc
- craigslist wichita ks
- craigslist rochester
- craigslist az
- craigslist vancouver wa
- craigslist prescott
- craigslist ann arbor
- nashville craigslist
- craigslist sioux falls
- craigslist charleston sc
- craigslist roanoke va
- orlando craigslist
- craigslist.org
- craigslist medford oregon
- detroit craigslist
- craigslist rockford
- craigslist north jersey
- charlotte craigslist
- craigslist space coast
- craigslist phoenix az
- tampa craigslist
- knoxville craigslist
- craigslist little rock
- craigslist bend oregon
- hudson valley craigslist
- craigslist kauai
- craigslist santa maria
- bend craigslist
- craigslist apartments
- craigslist fayetteville ar
- craigslist mcallen tx
- craigslist arkansas
- craigslist dayton ohio
- craigslist north bay
- albany craigslist
- craigslist oklahoma
- craigslist olympia
- bellingham craigslist
- el paso craigslist
- craigslist arizona
- redding craigslist
- craigslist winston salem
- craigslist honolulu
- craigslist indiana
- albuquerque craigslist
- craigslist binghamton
- craigslist treasure coast
- syracuse craigslist
- craigslist alabama
- craigslist huntsville
- craigslist daytona
- craigslist mankato
- craigslist richmond
- craigslist lansing
- craigslist new mexico
- craigslist waco
- craigslist massachusetts
- rochester craigslist
- craigslist syracuse ny
- madison craigslist
- craigslist utica
- salem craigslist
- craigslist flint
- inland empire craigslist
- craigslist birmingham al
- craigslist san antonio tx
- craigslist sc
- ocala craigslist
- south jersey craigslist
- craigslist md
- craigslist li
- craigslist kalamazoo
- missoula craigslist
- craigslist jackson tn
- craigslist yuma
- vt craigslist
- minneapolis craigslist
- craigslist flagstaff
- cleveland craigslist
- asheville craigslist
- craigslist harrisburg
- craigslist east bay
- craigslist montana
- craigslist lincoln
- craigslist east texas
- craigslist northern michigan
- craigslist wyoming
- craigslist lincoln ne
- craigslist new haven
- craigslist lancaster pa
- space coast craigslist
- craigslist visalia
- craigslist missouri
- craigslist south bend
- craigslist erie pa
- craigslist gainesville fl
- yakima craigslist
- craigslist sf bay area
- craigslist sioux city
- craigslist cars for sale
- craigslist houses for rent
- modesto craigslist
- craigslist youngstown
- craigslist stl
- craigslist charleston
- craigslist twin falls
- ventura craigslist
- craigslist baton rouge
- craigslist gold country
- craigslist duluth mn
- craigslist charlottesville
- craigslist cars for sale by owner
- louisville craigslist
- craigslist quad cities
- fargo craigslist
- craigslist tijuana
- craigslist western ma
- craigslist ky
- craigslist savannah
- craigslsit
- cregslist
- chico craigslist
- craigslist east idaho
- orange county craigslist
- craigslist jersey shore
- omaha craigslist
- long island craigslist
- okc craigslist
- craigslist topeka
- craigslist daytona beach
- mn craigslist
- craigslist la crosse
- craigslist northern va
- baltimore craigslist
- craigslist tn
- st louis craigslist
- craigslist fayetteville nc
- craigslist lehigh valley
- humboldt craigslist
- craigslist brooklyn
- craigslist cedar rapids
- craigslist killeen
- craigslist st. louis
- craigslist lancaster
- craigslist amarillo
- craigslist new hampshire
- craigslist joplin
- western mass craigslist
- craigslist mobile al
- craigslist vermont
- craigslist west palm beach
- yuma craiglist
- richmond craigslist
- columbus craigslist
- craig list
- craigslist big island
- craigslist ga
- craigslist long beach
- sarasota craigslist
- craigslist mpls
- craigslist houston tx
- craigslist watertown ny
- craigslist skagit
- craigslist abq
- craigslist st cloud
- craigslist fort lauderdale
- mcallen craigslist
- criagslist
- colorado springs craigslist
- craigslist kpr
- craigslist greensboro
- craigslist oregon coast
- craigslist jackson ms
- kc craigslist
- craigslist roanoke
- wichita craigslist
- dayton craigslist
- dc craigslist
- mankato craigslist
- billingscraigslist
- craigslist pittsburgh pa
- craigslist alaska
- craigslist huntsville al
- craigslist lynchburg va
- craigslist dubuque
- craigslist el paso tx
- kansas city craigslist
- craigslist virginia
- craigslist st louis mo
- craigslist dallas tx
- philadelphia craigslist
- craiglist mankato
- craigslist peoria il
- craigslist farmington nm
- craigslist wi
- pensacola craigslist
- craigslist athens ga
- fort myers craigslist
- craigslist ithaca
- craigslist merced
- craigslist nothern mi
- craigslist memphis tn
- wenatchee craigslist
- craigslist boise idaho
- craigslist springfield il
- sac craigslist
- craigslist muskegon
- craigslist hickory nc
- craigslist kentucky
- craigslist oklahoma city
- craigslist atlanta ga
- craigslist ft myers
- craigslist birmingham
- craigslist evansville
- craigslist free
- craigslist scranton
- craigslist illinois
- craigslist akron ohio
- craigslist brownsville
- craigslist fredericksburg va
- western slope craigslist
- florida craigslist
- craigslist san antonio texas
- craigslist nashville tn
- craigslist mo
- craigslist harrisburg pa
- craigslist connecticut
- craigslist santa rosa
- anchorage craigslist
- miami craigslist
- tri cities craigslist
- craigslist billings mt
- craigslist fairbanks
- craigslist san diego ca
- craigslist las vegas nv
- craigslist st augustine
- craigslist st cloud mn
- craigslist georgia
- norfolk craigslist
- skagit craigslist
- craigslist central nj
- slo craigslist
- craigslist kansas
- craigslist hartford
- greenville craigslist
- craigslist springfield missouri
- la craigslist
- craiglist kalispell
- craiglist abq
- craigslist idaho
- fort collins craigslist
- craigslist north carolina
- craigslit
- craigslist roseburg
- bozeman craigslist
- craig’s list
- craigslist washington dc
- wausau craigslist
- craigslist billings
- craigslist rapid city
- maui craigslist
- craigslist/longisland
- harrisburg craigslist
- craigslist mobile
- craigslist virginia beach
- kalispell craigslist
- craigslist shreveport
- santa fe craigslist
- roanoke craigslist
- bakersfield craigslist
- billings craigslist
- craigslist dothan al
- grand rapids craigslist
- las cruces craigslist
- craigslist helena
- nj craigslist
- rochester minnesota craigslist
- craigslist harrisonburg
- cape cod craigslist
- hartford craigslist
- nyc craigslist
- craigslist of san francisco bay area
- craigslist sheboygan
- craigslist eastern shore
- daytona craigslist
- craigslist vancouver
- craigslist glens falls
- craiglist roseburg
- craigslist d
- craigslist search by state
- wyoming craigslist
- craigslist hartford ct
- vermont craigslist
- craigslisteasternnc
- craigslist mesa az
- craigslist milwaukee wi
- craigslist northern wi
- craigslist maryland
- craigslist klamath falls
- craigslist panama city fl
- east idaho craigslist
- craigslist riverside
- delaware craigslist
- craigslist fort smith
- pueblo craigslist
- craiglist elmira
- eau claire craigslist
- craigslist staten island
- craigslist tennessee
- craigslist puppies
- craigslist utah
- craigslist brainerd
- craigslist augusta ga
- craigslist nebraska
- craigslist northern mi
- craigslist eastern ct
- craigslist sac
- craigslist kenosha
- fort wayne craigslist
- corvallis craigslist
- craigslist hickory
- craigslist allentown pa
- craigslist texoma
- craigslist reading pa
- craigslist elmira
- craigslist south carolina
- craigslist in new mexico
- waco craigslist
- craigslist utica ny
- myrtle beach craigslist
- new york craigslist
- binghamton craigslist
- jacksonville craigslist
- treasure coast craigslist
- craigslist iowa city
- stl craigslist
- craigslist albuquerque nm
- craigslist tri cities tn
- prescott craigslist
- craigslist tampa bay
- craigslist new yotk
- craigslist college station
- craigslist up
- craigslist sd
- craigslist dothan
- craigslist bradenton
- oahu craigslist
- east texas craigslist
- craigs list fort wayne
- san francisco craigslist
- craigslist ca
- craigslist des moines iowa
- monterey craigslist
- craigslist annapolis
- craigslist state college
- north jersey craigslist
- craigslist tucson az
- green bay craigslist
- cregs list
- greensboro craigslist
- southbendcraigslist
- santa barbara craigslist
- craigslist bemidji
- craigslist madison wi
- craigslist gigs
- craigslist prescott az
- craigslist gulfport
- chattanooga craigslist
- crigslist
- duluth craigslist
- lubbock craigslist
- craigslist columbus ga
- craigslist macon
- craigslist la crosse wi
- craigslist salt lake city
- ri craigslist
- craigslist sites
- ny craigslist
- amarillo craigslist
- appleton craigslist
- craigslist.com
- craiglist chicago
- craigslist cincinnati ohio
- craigslist roseburg oregon
- craigslist okaloosa
- arkansas craigslist
- stockton craigslist
- sf bay craigslist
- craigslist brownsville tx
- ie craigslist
- craigslist st paul
- criaglist
- abq craigslist
- corpus christi craigslist
- craigslist nwi
- worcester craigslist
- craigslist great falls
- memphis craigslist
- craigslist bay area san francisco
- craiglist wausau
- criglist
- utica craigslist
- craigslist scranton pa
- craiglsit
- nycraigslist.
- craigslist apartments for rent
- craigslist dfw
- craigslist janesville
- craigslist eugene oregon
- craigslist rooms for rent
- craigslist winston salem nc
- texas craigslist
- craiglist sac
- indianapolis craigslist
- craigslist winchester va
- craigslist saginaw
- craigslist sf bay
- craigslist southern illinois
- quad cities craigslist
- craigslist williamsport
- craigslist grand rapids mi
- craigslist olympic peninsula
- craigslist ft wayne in
- craigslist norfolk va
- eastern nc craigslist
- craigslist southcoast
- craigslist springfield
- craigslist frederick md
- craigslist hilo
- joplin craigslist
- yuma craigslist
- craigslist macon ga
- st cloud craigslist
- craigslistnh
- boulder craigslist
- craigslist san francisco bay area
- craigslist abilene
- craigslist altoona
- craigslist spacecoast
- craigslist mohave county
- craigslist naples fl
- craigslist spokane wa
- l i craigslist
- craigslist eastern oregon
- craigslist louisiana
- craigslist fort smith ar
- craigslist clarksville tn
- craigslist mansfield ohio
- craigslist grand forks
- craigslist u p
- craigslist so illinois
- tri cities craigslist tennessee
- craigslist pennsylvania
- craigslist mi grand rapids
- craigslist tyler texas
- craigslist oakland
- baton rouge craigslist
- craigslist fl
- montana craigslist
- bend or craigslist
- craigslist jacksonville florida
- craigslist lynchburg
- mpls craigslist
- craigslist myrtle beach sc
- ithaca craigslist
- craigslist northern virginia
- craigs list eastern nc
- oregon craigslist
- craigslist eau claire wi
- craigslist long island ny
- creglist
- youngstown craigslist
- greiglist la
- sfbaycraigslist
- sd craigslist
- akron canton craigslist
- mcallen texas craigslist
- springfield craigslist
- craigslist tricities
- helena craigslist
- craigslist rochester new york
- craigslist easternshore
- lakeland craigslist
- licraigslist
- craigslist los angeles ca
- craigslist medford or
- www craigslist com
- craigslistkpr
- craigslist fayetteville
- craigslist gainesville
- watertown craigslist
- craigslist lexington
- craigslist modesot
- toledo craigslist
- rockford craigslist
- craigslist panama city
- craigslist broward
- craigslist motorcycles
- craigslist kennewick
- sac craiglist
- arizona craigslist
- craigs list bend or
- craiglist houston
- roseburg craigslist
- lexington craigslist
- visalia craigslist
- craigslist asheville nc
- craigslist binghamton ny
- quadcities craigslist
- creigslist
- craigslist lewiston
- charleston craigslist
- chicagocraigs list
- northern michigan craigslist
- kpr craigslist
- craigslist cars and trucks
- new orleans craigslist
- craigslist s.d.
- craigslist port huron
- washington dc craigslist
- phoenix.craigslist
- craigslist car
- craigslist jackson michigan
- craigslist mohave
- cragislist
- south florida craigslist
- craigslist sierra vista
- portland.craigslist
- flagstaff craigslist
- santa cruz craigslist
- craigslist grand island
- lynchburg craigslist
- oklahoma craigslist
- craiglist helena
- craiglist utica
- craigslist cars for sale by owner near me
- craigslist south coast
- craigslist canton ohio
- craigslist fredericksburg
- craigslis
- craigslist hampton roads
- craigslist wv
- michigan craigslist
- craigslist youngstown ohio
- ohio craigslist
- ct craigslist
- craigslist kansas city mo
- kauai craigslist
- craigslist semo
- minneapolis.craigslist
- craigslist san marcos
- brownsville texas craigslist
- lynchburg virginia craigslist
- craigslist plattsburgh ny
- nc craigslist
- craigslist fort myers florida
- craigslist fayetteville arkansas
- craigslist high rockies
- craigslist houston pets
- craigslist org
- craigslistpueblo
- craislist
- craigslist texarkana
- craigslist north ms
- craigslist kcmo
- craigslist florence sc
- sf bay area craigslist
- oregon coast craigslist
- craigslist tyler tx
- craigslist de
- craigslist wichita falls
- craigslist st joseph mo
- denver.craigslist
- craigslist dallas texas
- craigslist lewiston idaho
- craigslist in york pa
- gold country craigslist
- craigslist bowling green ky
- bay area craigslist
- craiglist lincoln nebraska
- craigslist san bernardino
- brainerd craigslist
- craigslist lafayette la
- sioux city craigslist
- frederick craigslist
- craigslist missed connections
- fairbanks craigslist
- craigslist odessa
- craigslist joplin mo
- craigslist odessa tx
- craigslist of san luis obispo
- craiglist twin falls
- craigslist houston texas
- eastern oregon craigslist
- craigslist fairfield ct
- craigslist phoenix pets
- youngstown craiglist
- new haven craigslist
- craigslist mississippi
- craigslist yuba sutter
- craigslist jacksonville nc
- huntsville craigslist
- craigslist plattsburgh
- craigslist jackson mi
- craigslist st george
- craigslist augusta
- craigslist me
- craigslist nueva york
- craigslist.
- craigslist fort myers fl
- craigslist nj central
- merced craigslist
- craigslist lima ohio
- craigs list denver
- hawaii craigslist
- palm springs craigslist
- craigslist phoenix arizona
- craigslist austin texas
- colorado craigslist
- craigslist lafayette indiana
- craigslist tri-cities
- craigslist dallas pets
- craigslist terre haute
- craigslist brainerd mn
- rapid city craigslist
- california craigslist
- craigslist mi
- craigslist yuba city
- roanoke craiglist
- upcraigslist
- craigslist blacksburg
- craigslist tri cities wa
- craigslist bloomington
- sioux falls craigslist
- yuba sutter cragslist
- craigslist athens
- craigslist allentown
- craigslist free stuff near me
- craigslist nm
- craigslsit eastern nc
- craigslist lansing mi
- craigslist victoria tx
- craigslist fresno ca
- craigslist kenai
- pa craigslist
- craigslist cleveland ohio
- craigslist portland or
- craigs list maine
- elmira craigslist
- tallahassee craigslist
- craigslist reno nv
- craigslist yuma az
- up craigslist
- craigslist toledo ohio
- craigslist north wisconsin
- craigslist albany oregon
- www.craigslist.com


![How to Fix [pii_email_d4d3f5b9d7f3c8b22729] Outlook Error How to Fix [pii_email_d4d3f5b9d7f3c8b22729] Outlook Error](https://www.webtechgalaxy.com/wp-content/uploads/2021/10/How-to-Fix-pii_email_d4d3f5b9d7f3c8b22729-Outlook-Error-768x512.webp)







![[Solved] – [pii_email_7626800840576d24b18c] Email Error Code [Solved] – [pii_email_7626800840576d24b18c] Email Error Code](https://www.webtechgalaxy.com/wp-content/uploads/2021/10/error-9-768x512.jpg)